D^3CTF 2019 KeyGenMe WP
Category: RE
Solved: 1
那道题稍微看了一下,无符号、大数运算,strings出了一些字符串,估计是用了库。
搜github找到用的是miracl,开始了漫长的恢复符号表之旅…试了rizzo、flair,恢复率很低…
后来搜某字符串搜到了源码…
https://github.com/BingyZhang/EC-ElGamal/blob/252d57cae7a72019fbc08ce644b60a54014761be/dssver.c
标记对应的函数,看与标准实现之间的区别。
发现在生成的时候,dssign签名了两次,
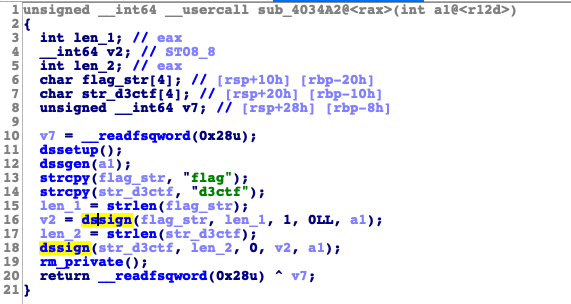
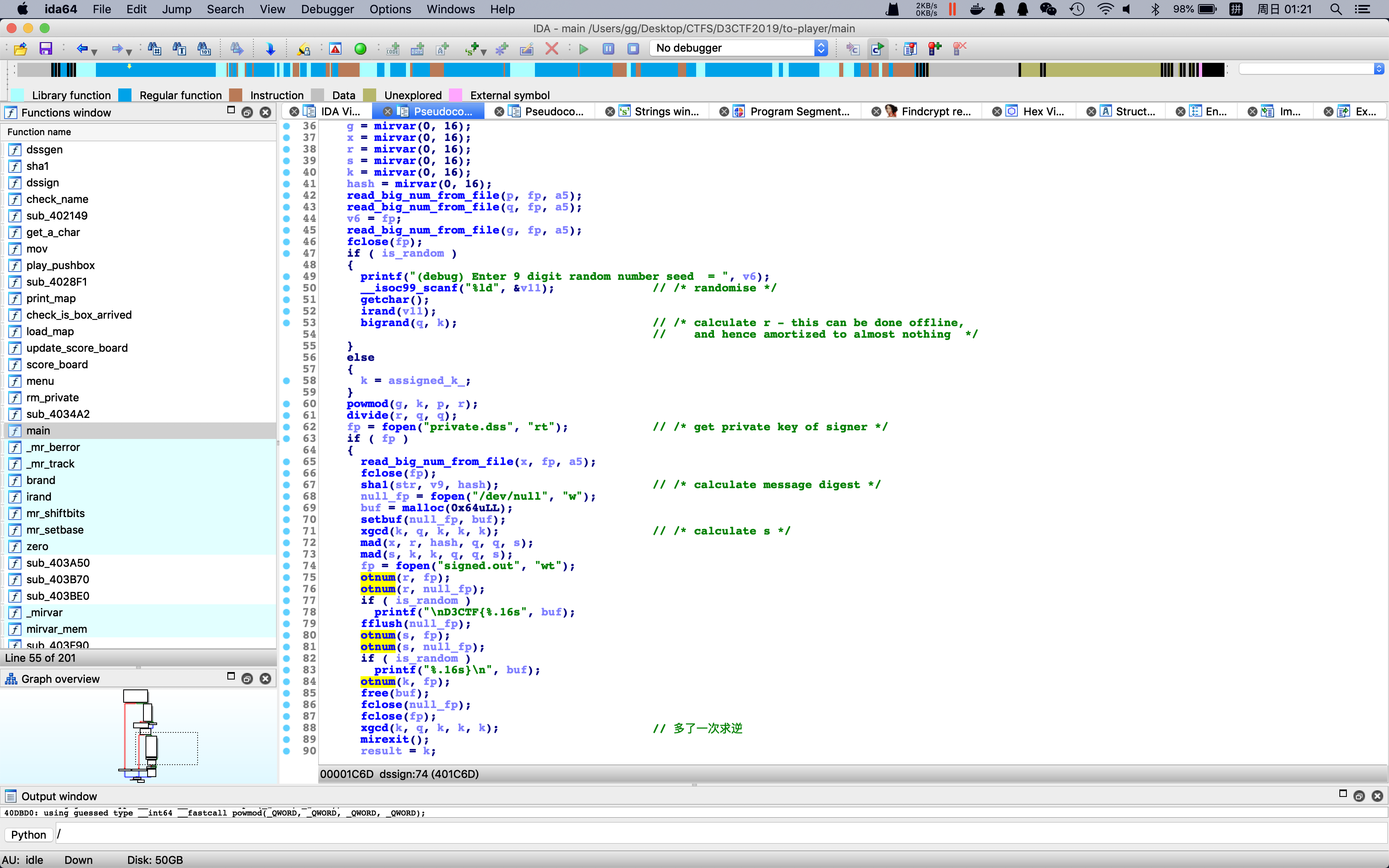
发现k重复使用,且输出到了signed.out
根据DSA签名算法

其他信息都有,我们可以恢复出x了。然后根据x求出’flag’的s
1 | from Crypto.Util.number import * |